General Information
The repository for this application (open on GitHub) has 1680 stars and was forked 913 times. The codebase consists of 2328 lines of code and makes use of the following technologies:
Docker Compose Eureka Gradle Hystrix Ribbon Spring Config Spring OAuth Zuul
Data Flow Diagram
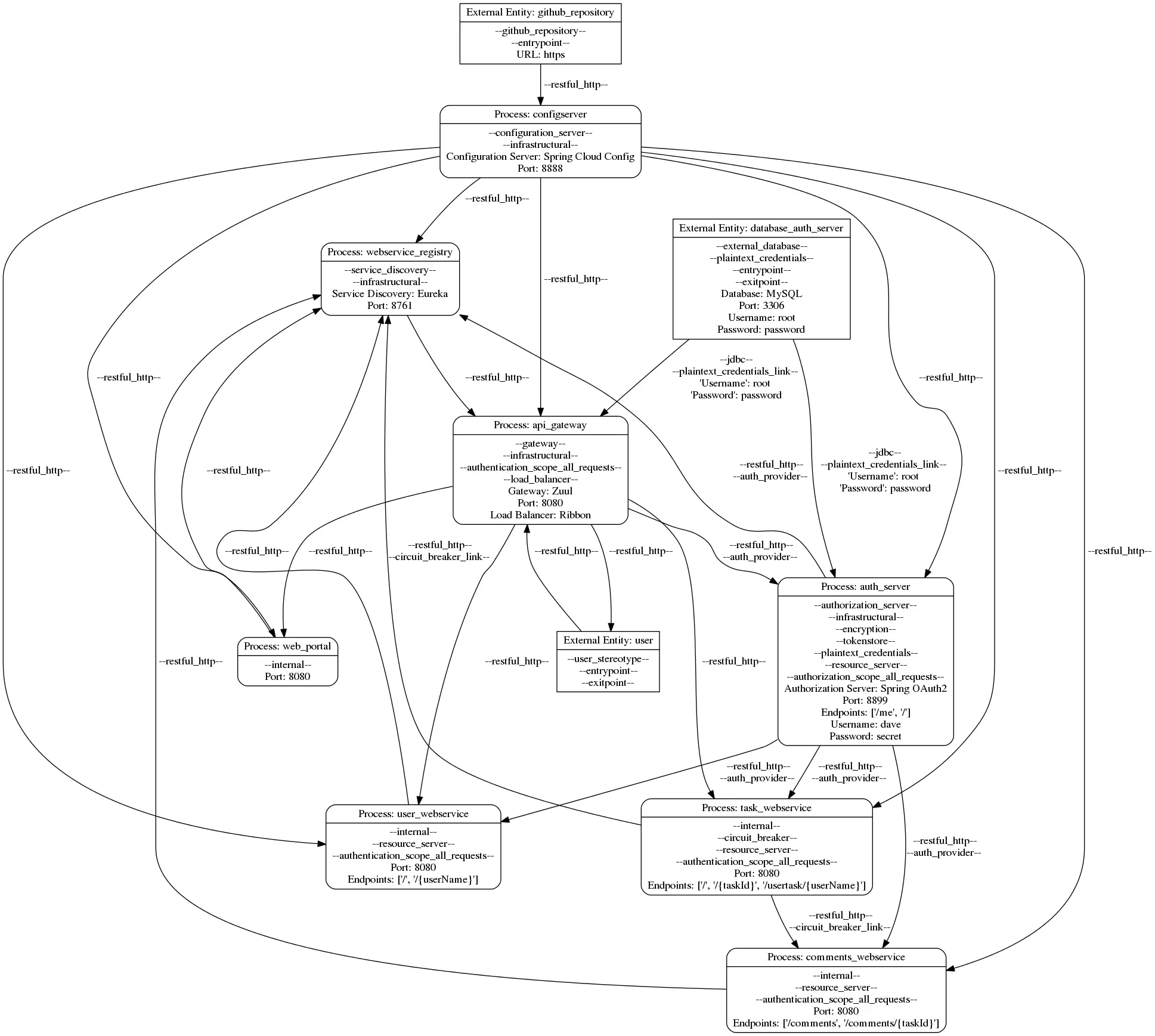
Download the following model file here. Other formats are provided below.
{
"services": [
{
"name": "configserver",
"stereotypes": [
"configuration_server",
"infrastructural"
],
"tagged_values": {
"Configuration Server": "Spring Cloud Config",
"Port": 8888
}
},
{
"name": "webservice_registry",
"stereotypes": [
"service_discovery",
"infrastructural"
],
"tagged_values": {
"Service Discovery": "Eureka",
"Port": 8761
}
},
{
"name": "auth_server",
"stereotypes": [
"authorization_server",
"infrastructural",
"encryption",
"tokenstore",
"plaintext_credentials",
"resource_server",
"authorization_scope_all_requests"
],
"tagged_values": {
"Authorization Server": "Spring OAuth2",
"Port": 8899,
"Endpoints": [
"/me",
"/"
],
"Username": "dave",
"Password": "secret"
}
},
{
"name": "web_portal",
"stereotypes": [
"internal"
],
"tagged_values": {
"Port": 8080
}
},
{
"name": "user_webservice",
"stereotypes": [
"internal",
"resource_server",
"authentication_scope_all_requests"
],
"tagged_values": {
"Port": 8080,
"Endpoints": [
"/",
"/{userName}"
]
}
},
{
"name": "comments_webservice",
"stereotypes": [
"internal",
"resource_server",
"authentication_scope_all_requests"
],
"tagged_values": {
"Port": 8080,
"Endpoints": [
"/comments",
"/comments/{taskId}"
]
}
},
{
"name": "task_webservice",
"stereotypes": [
"internal",
"circuit_breaker",
"resource_server",
"authentication_scope_all_requests"
],
"tagged_values": {
"Port": 8080,
"Endpoints": [
"/",
"/{taskId}",
"/usertask/{userName}"
]
}
},
{
"name": "api_gateway",
"stereotypes": [
"gateway",
"infrastructural",
"authentication_scope_all_requests",
"load_balancer"
],
"tagged_values": {
"Gateway": "Zuul",
"Port": 8080,
"Load Balancer": "Ribbon"
}
}
],
"external_entities": [
{
"name": "github_repository",
"stereotypes": [
"github_repository",
"entrypoint"
],
"tagged_values": {
"URL": "https://github.com/anilallewar/sample-config"
}
},
{
"name": "database_auth_server",
"stereotypes": [
"external_database",
"plaintext_credentials",
"entrypoint",
"exitpoint"
],
"tagged_values": {
"Database": "MySQL",
"Port": 3306,
"Username": "root",
"Password": "password"
}
},
{
"name": "user",
"stereotypes": [
"user_stereotype",
"entrypoint",
"exitpoint"
],
"tagged_values": {}
}
],
"information_flows": [
{
"sender": "github_repository",
"receiver": "configserver",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "configserver",
"receiver": "webservice_registry",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "database_auth_server",
"receiver": "auth_server",
"stereotypes": [
"jdbc",
"plaintext_credentials_link"
],
"tagged_values": {
"'Username'": "\"root\"",
" 'Password'": "\"password\""
}
},
{
"sender": "configserver",
"receiver": "auth_server",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "auth_server",
"receiver": "webservice_registry",
"stereotypes": [
"restful_http",
"auth_provider"
],
"tagged_values": {}
},
{
"sender": "configserver",
"receiver": "web_portal",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "web_portal",
"receiver": "webservice_registry",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "configserver",
"receiver": "user_webservice",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "user_webservice",
"receiver": "webservice_registry",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "auth_server",
"receiver": "user_webservice",
"stereotypes": [
"restful_http",
"auth_provider"
],
"tagged_values": {}
},
{
"sender": "configserver",
"receiver": "comments_webservice",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "comments_webservice",
"receiver": "webservice_registry",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "auth_server",
"receiver": "comments_webservice",
"stereotypes": [
"restful_http",
"auth_provider"
],
"tagged_values": {}
},
{
"sender": "task_webservice",
"receiver": "webservice_registry",
"stereotypes": [
"restful_http",
"circuit_breaker_link"
],
"tagged_values": {}
},
{
"sender": "auth_server",
"receiver": "task_webservice",
"stereotypes": [
"restful_http",
"auth_provider"
],
"tagged_values": {}
},
{
"sender": "configserver",
"receiver": "task_webservice",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "task_webservice",
"receiver": "comments_webservice",
"stereotypes": [
"restful_http",
"circuit_breaker_link"
],
"tagged_values": {}
},
{
"sender": "user",
"receiver": "api_gateway",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "api_gateway",
"receiver": "user",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "api_gateway",
"receiver": "auth_server",
"stereotypes": [
"restful_http",
"auth_provider"
],
"tagged_values": {}
},
{
"sender": "database_auth_server",
"receiver": "api_gateway",
"stereotypes": [
"jdbc",
"plaintext_credentials_link"
],
"tagged_values": {
"'Username'": "\"root\"",
" 'Password'": "\"password\""
}
},
{
"sender": "api_gateway",
"receiver": "user_webservice",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "api_gateway",
"receiver": "task_webservice",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "api_gateway",
"receiver": "web_portal",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "configserver",
"receiver": "api_gateway",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "webservice_registry",
"receiver": "api_gateway",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
}
]
}
Model Items
The Application consists of a total of 137 elements:
| Element | Count |
|---|---|
| Services | 8 |
| External Entities | 3 |
| Information Flows | 26 |
| Annotations | 100 |
| Total Items | 137 |
Model Representations
Open the model in the following formats:
Traceability
Open the traceability information for all model items:
Security Rules
The following table shows the application’s adherence to the 17 architectural security rules. The last column provides model variants that adhere to the rule for each rule that is initially violated.
| Rule ID | Verdict | Evidence | Model Variant |
|---|---|---|---|
| R1 | Evidence | ||
| R2 | Evidence | ||
| R3 | Evidence | ||
| R4 | Evidence | Variant | |
| R5 | Evidence | ||
| R6 | Evidence | Variant | |
| R7 | Evidence | Variant | |
| R8 | Evidence | Variant | |
| R9 | Evidence | Variant | |
| R10 | Evidence | Variant | |
| R11 | Evidence | Variant | |
| R12 | Evidence | Variant | |
| R13 | Evidence | ||
| R14 | Evidence | ||
| R16 | Evidence | ||
| R17 | Evidence | Variant | |
| R18 | Evidence | Variant |
Evidence and explanations for rule decisions
R1
This rule is unknown:
- The @EnableZuulProxy annotation is present,
- The @EnableOAuth2Sso annotation is present,
- No routing to the authorization server as mentioned by author, thus no single entrypoint.
Artifacts:
R2
Rule is adhered to:
- The @EnableOAuth2Resource annotation is present at downstream services,
- Endpoint at authorization server in yml for authentication and authorization.
Artifacts:
- Application.java: Line: 47
- Application.java: Line: 41
- Application.java: Line: 40
- ResourceServerConfiguration.java: Line: 22
- comments-webservice.yml: Line: 16
R3
This rule is unknown:
- The @EnableAuthorizationServer annotation is present,
- No JwtAccessTokenConverter present, hence using opaque token,
- Endpoint for validating token and user present
Artifacts:
R4
This rule is unknown: As rule 2 already confirms that every downstream service needs tokens for authorization/authentication. However, no evidence of tokens transferred to internal identity representations.
R5
Rule is adhered to: Tokens are validated based on the endpoint at the auth server.
Artifacts:
- comments-webservice.yml: Line: 16
R6
Rule is violated: No blocking mechanism in place for multiple failed login attempts.
R7
Rule is violated: No mention of SSL, TLS, keystores or trust-stores in application.
R8
Rule is violated: See rule 7.
R9
Rule is violated: No central logging system is deployed.
R10
Rule is violated: See rule 9.
R11
Rule is violated: See rule 9.
R12
Rule is violated: See rule 9.
R13
Rule is adhered to: The @EnableZuulProxy annotation at the API gateway enables Hystrix and its circuit breaker functionality.
Artifacts:
- Application.java: Line: 51
R14
Rule is adhered to: The @EnableZuulProxy annotation at the API gateway enables Ribbon and its load balancing functionality.
Artifacts:
- Application.java: Line: 51
R15
This rule is not applicable: Not a service mesh deployment.
R16
Rule is adhered to:
- Registry Service (Eureka Server) with @EnableEurekaServer present.
- Started in Docker Container through Compose, thus deployable on dedicated server
Artifacts:
R17
Rule is violated: No HTTP basic password listed in any YML-Configuration of format username:password@here-location-of-eureka-server at “eureka.client.serviceUrl.defaultZone”.
Artifacts:
- comments-webservice.yml: Line: 26
R18
Rule is violated: No secret manager is deployed.