General Information
The repository for this application (open on GitHub) has 310 stars and was forked 317 times. The codebase consists of 14527 lines of code and makes use of the following technologies:
Consul Docker Docker Compose Elasticsearch Kibana Logstash Nginx RabbitMQ Weave Scope Zuul
Data Flow Diagram
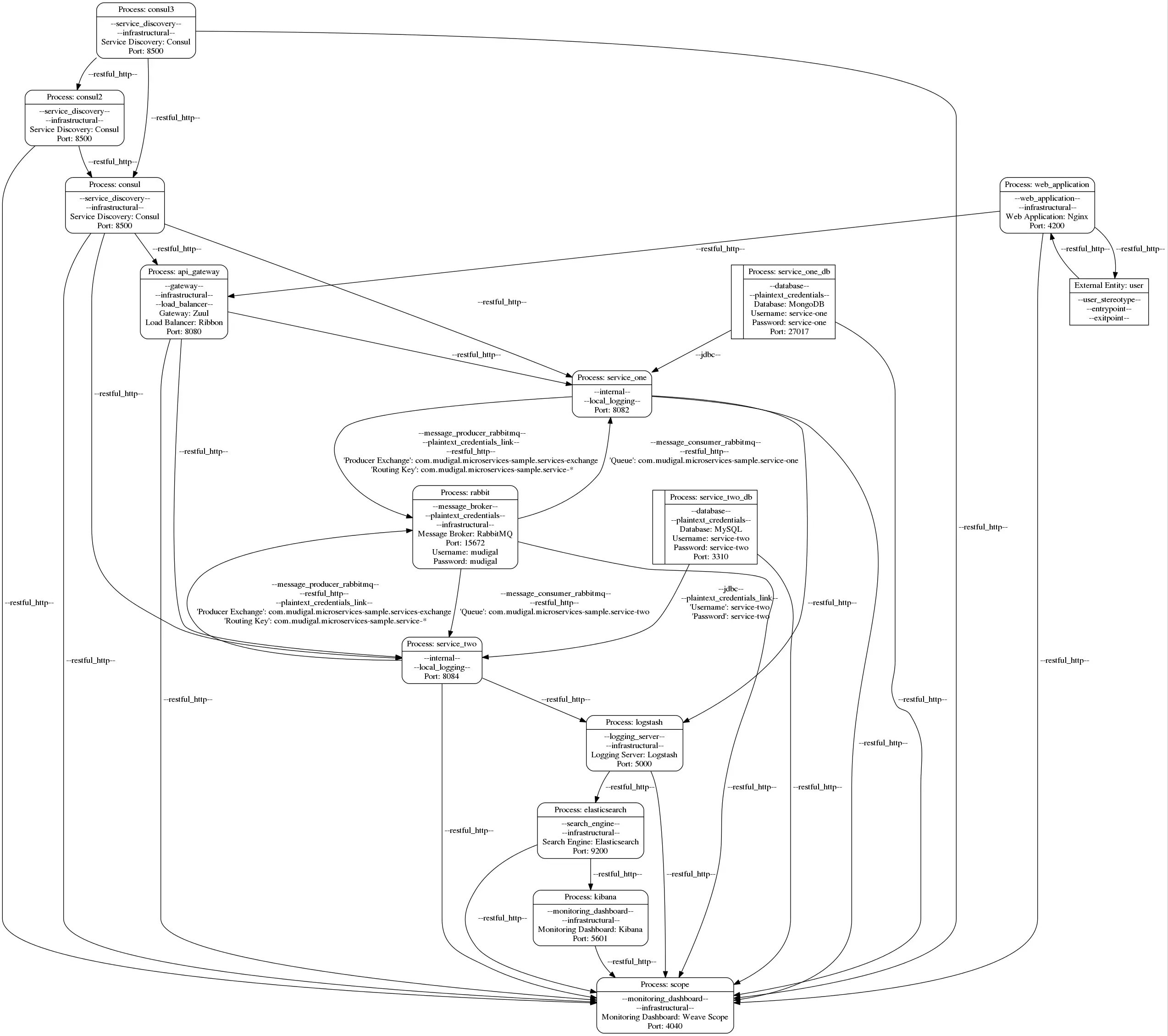
Download the following model file here. Other formats are provided below.
{
"services": [
{
"name": "consul",
"stereotypes": [
"service_discovery",
"infrastructural"
],
"tagged_values": {
"Service Discovery": "Consul",
"Port": 8500
}
},
{
"name": "consul2",
"stereotypes": [
"service_discovery",
"infrastructural"
],
"tagged_values": {
"Service Discovery": "Consul",
"Port": 8500
}
},
{
"name": "consul3",
"stereotypes": [
"service_discovery",
"infrastructural"
],
"tagged_values": {
"Service Discovery": "Consul",
"Port": 8500
}
},
{
"name": "elasticsearch",
"stereotypes": [
"search_engine",
"infrastructural"
],
"tagged_values": {
"Search Engine": "Elasticsearch",
"Port": 9200
}
},
{
"name": "logstash",
"stereotypes": [
"logging_server",
"infrastructural"
],
"tagged_values": {
"Logging Server": "Logstash",
"Port": 5000
}
},
{
"name": "kibana",
"stereotypes": [
"monitoring_dashboard",
"infrastructural"
],
"tagged_values": {
"Monitoring Dashboard": "Kibana",
"Port": 5601
}
},
{
"name": "rabbit",
"stereotypes": [
"message_broker",
"plaintext_credentials",
"infrastructural"
],
"tagged_values": {
"Message Broker": "RabbitMQ",
"Port": 15672,
"Username": "mudigal",
"Password": "mudigal"
}
},
{
"name": "service_one",
"stereotypes": [
"internal",
"local_logging"
],
"tagged_values": {
"Port": 8082
}
},
{
"name": "service_two",
"stereotypes": [
"internal",
"local_logging"
],
"tagged_values": {
"Port": 8084
}
},
{
"name": "service_one_db",
"stereotypes": [
"database",
"plaintext_credentials"
],
"tagged_values": {
"Database": "MongoDB",
"Username": "service-one",
"Password": "service-one",
"Port": 27017
}
},
{
"name": "service_two_db",
"stereotypes": [
"database",
"plaintext_credentials"
],
"tagged_values": {
"Database": "MySQL",
"Username": "service-two",
"Password": "service-two",
"Port": 3310
}
},
{
"name": "api_gateway",
"stereotypes": [
"gateway",
"infrastructural",
"load_balancer"
],
"tagged_values": {
"Gateway": "Zuul",
"Load Balancer": "Ribbon",
"Port": 8080
}
},
{
"name": "web_application",
"stereotypes": [
"web_application",
"infrastructural"
],
"tagged_values": {
"Web Application": "Nginx",
"Port": 4200
}
},
{
"name": "scope",
"stereotypes": [
"monitoring_dashboard",
"infrastructural"
],
"tagged_values": {
"Monitoring Dashboard": "Weave Scope",
"Port": 4040
}
}
],
"information_flows": [
{
"sender": "consul2",
"receiver": "consul",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "consul3",
"receiver": "consul",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "consul3",
"receiver": "consul2",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "logstash",
"receiver": "elasticsearch",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "elasticsearch",
"receiver": "kibana",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "consul",
"receiver": "service_one",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "service_one",
"receiver": "logstash",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "service_one",
"receiver": "rabbit",
"stereotypes": [
"message_producer_rabbitmq",
"plaintext_credentials_link",
"restful_http"
],
"tagged_values": {
"'Producer Exchange'": "\"com.mudigal.microservices-sample.services-exchange\"",
" 'Routing Key'": "\"com.mudigal.microservices-sample.service-*\""
}
},
{
"sender": "rabbit",
"receiver": "service_one",
"stereotypes": [
"message_consumer_rabbitmq",
"restful_http"
],
"tagged_values": {
"'Queue'": "\"com.mudigal.microservices-sample.service-one\""
}
},
{
"sender": "consul",
"receiver": "service_two",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "service_two",
"receiver": "logstash",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "service_two",
"receiver": "rabbit",
"stereotypes": [
"message_producer_rabbitmq",
"restful_http",
"plaintext_credentials_link"
],
"tagged_values": {
"'Producer Exchange'": "\"com.mudigal.microservices-sample.services-exchange\"",
" 'Routing Key'": "\"com.mudigal.microservices-sample.service-*\""
}
},
{
"sender": "rabbit",
"receiver": "service_two",
"stereotypes": [
"message_consumer_rabbitmq",
"restful_http"
],
"tagged_values": {
"'Queue'": "\"com.mudigal.microservices-sample.service-two\""
}
},
{
"sender": "service_one_db",
"receiver": "service_one",
"stereotypes": [
"jdbc"
],
"tagged_values": {}
},
{
"sender": "service_two_db",
"receiver": "service_two",
"stereotypes": [
"jdbc",
"plaintext_credentials_link"
],
"tagged_values": {
"'Username'": "\"service-two\"",
" 'Password'": "\"service-two\""
}
},
{
"sender": "api_gateway",
"receiver": "service_one",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "api_gateway",
"receiver": "service_two",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "consul",
"receiver": "api_gateway",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "user",
"receiver": "web_application",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "web_application",
"receiver": "user",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "web_application",
"receiver": "api_gateway",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "api_gateway",
"receiver": "scope",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "service_one",
"receiver": "scope",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "service_one_db",
"receiver": "scope",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "service_two",
"receiver": "scope",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "service_two_db",
"receiver": "scope",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "web_application",
"receiver": "scope",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "rabbit",
"receiver": "scope",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "consul",
"receiver": "scope",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "consul2",
"receiver": "scope",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "consul3",
"receiver": "scope",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "kibana",
"receiver": "scope",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "elasticsearch",
"receiver": "scope",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "logstash",
"receiver": "scope",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
}
],
"external_entities": [
{
"name": "user",
"stereotypes": [
"user_stereotype",
"entrypoint",
"exitpoint"
],
"tagged_values": {}
}
]
}
Model Items
The Application consists of a total of 164 elements:
| Element | Count |
|---|---|
| Services | 14 |
| External Entities | 1 |
| Information Flows | 34 |
| Annotations | 115 |
| Total Items | 164 |
Model Representations
Open the model in the following formats:
Traceability
Open the traceability information for all model items:
Security Rules
The following table shows the application’s adherence to the 17 architectural security rules. The last column provides model variants that adhere to the rule for each rule that is initially violated.
| Rule ID | Verdict | Evidence | Model Variant |
|---|---|---|---|
| R1 | Evidence | ||
| R2 | Evidence | Variant | |
| R3 | Evidence | Variant | |
| R4 | Evidence | Variant | |
| R5 | Evidence | Variant | |
| R6 | Evidence | Variant | |
| R7 | Evidence | Variant | |
| R8 | Evidence | Variant | |
| R9 | Evidence | ||
| R10 | Evidence | ||
| R11 | Evidence | Variant | |
| R12 | Evidence | Variant | |
| R13 | Evidence | ||
| R14 | Evidence | ||
| R16 | Evidence | ||
| R17 | Evidence | Variant | |
| R18 | Evidence | Variant |
Evidence and explanations for rule decisions
R1
Rule is partially adhered to: User only communicates with the NGINX proxy, that proxies all requests. There is no indication of requests being authenticated/authorized at the NGINX Proxy.
Additionally, there is a Spring Cloud Zuul Gateway present, which also does not authenticate/authorize any requests.
Artifacts:
R2
Rule is violated: The services do not authenticate requests mutually. No client authentication is configured and no authentication header is used.
R3
Rule is violated: No authentication mechanism is deployed.
R4
Rule is violated: External entities are not represented in the application. Users behave transparent to the server.
R5
Rule is violated: No authentication tokens are used.
R6
Rule is violated: No rate limiting of any means is deployed.
R7
Rule is violated: User external entities can call the gateway service using an unencrypted HTTP connection.
R8
Rule is violated: All internal services communicate over insecure HTTP connections.
Artifacts:
- gateway.service.ts: Line: 13
R9
Rule is adhered to: This microservice application deploys the ELK stack (Elasticsearch, Logstash, Kibana) as a logging mechanism. Logstash is deployed as a central logging subsystem. Logstash then sends the formatted data to an Elasticsearch indexing server. Additionally Kibana is deployed as a monitoring dashboard on top of the indexing server.
Artifacts:
R10
Rule is adhered to: Both service containers and the API gateway deploy local logging agents. The services use logback as a local logging agent to send the collected log files from the spring servers to the central logstash server.
Artifacts:
R11
Rule is violated: No explicit log sanitization is deployed. Even though no API keys or PII are written to any log in this application, this rule is still considered disregarded because the string data sent via RabbitMQ is directly logged without local checking (see exemplary artifacts).
Artifacts:
R12
Rule is violated: The communication between logging agents is not brokered by any message broker. The deployed RabbitMQ broker only handles service queues, not logging calls. The logs are not encrypted during transmission and not mutually authenticated, nor is any availability ensured apart from container startup dependencies.
Artifacts:
- logback.xml: Line: 23
R13
Rule is adhered to: The Zuul API gateway includes the Hystrix Circuit Breaker functionality.
Artifacts:
- ApiGatewayApplication.java: Line: 17
R14
Rule is adhered to: The Zuul API gateway performs load balancing using Ribbon by default.
Artifacts:
- ApiGatewayApplication.java: Line: 17
R15
This rule is not applicable: Not a service mesh deployment.
R16
Rule is adhered to: Consul is deployed as a service registry.
Artifacts:
- RegistryApplication.java: Line: 19
R17
Rule is violated: Registration with the Consul server is not secured using access tokens or access control lists.
Artifacts:
R18
Rule is violated: No secret manager is deployed. Passwords are either deployed in plaintext in the Docker Compose configuration or in the Spring Boot configuration.
Artifacts: