General Information
The repository for this application (open on GitHub) has 308 stars and was forked 231 times. The codebase consists of 5283 lines of code and makes use of the following technologies:
Docker Docker Compose Eureka Hystrix Kafka Logstash Maven Nginx Spring Admin Spring Config Spring OAuth ZooKeeper
Data Flow Diagram
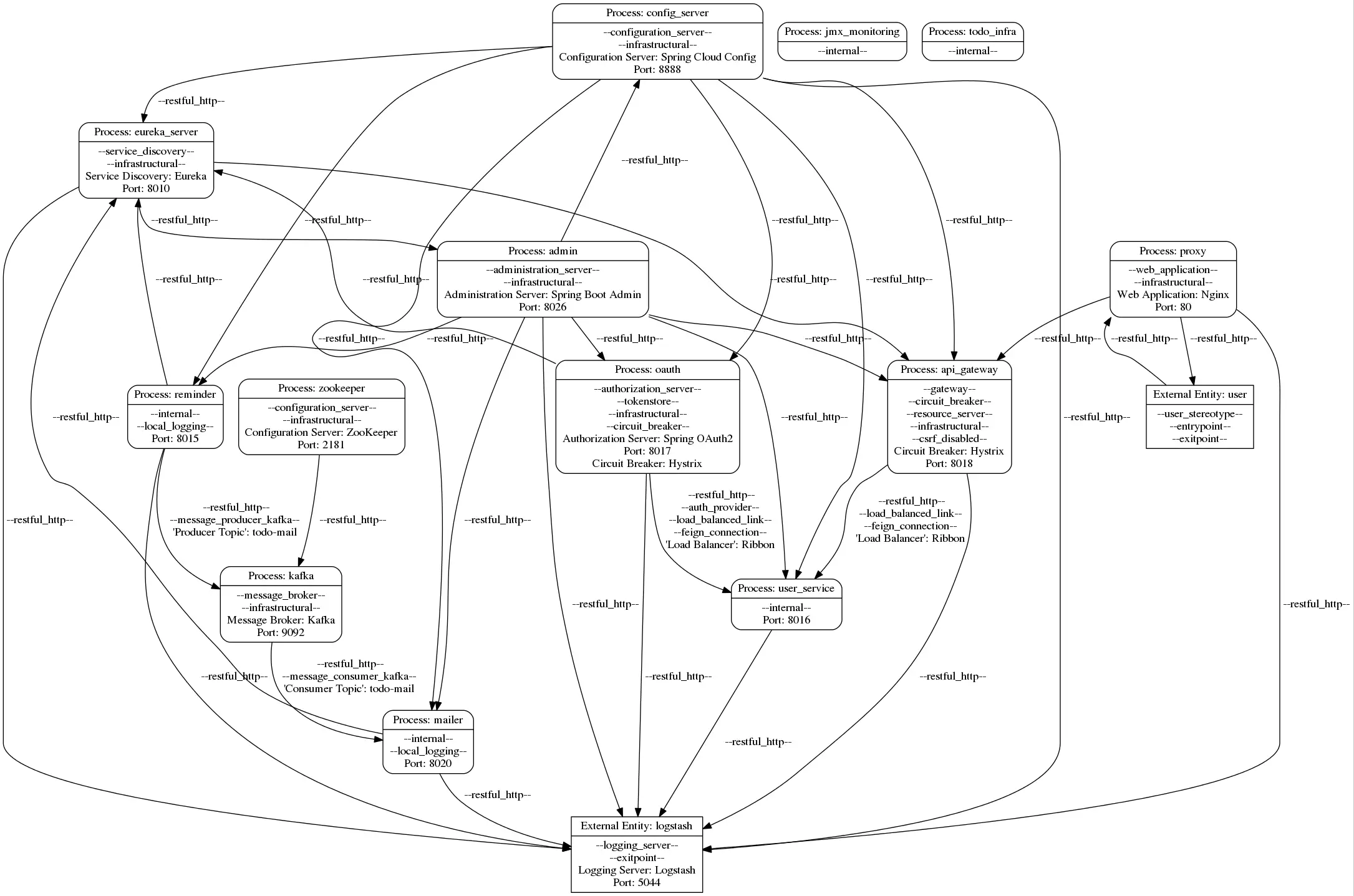
Download the following model file here. Other formats are provided below.
{
"services": [
{
"name": "config_server",
"stereotypes": [
"configuration_server",
"infrastructural"
],
"tagged_values": {
"Configuration Server": "Spring Cloud Config",
"Port": 8888
}
},
{
"name": "admin",
"stereotypes": [
"administration_server",
"infrastructural"
],
"tagged_values": {
"Administration Server": "Spring Boot Admin",
"Port": 8026
}
},
{
"name": "eureka_server",
"stereotypes": [
"service_discovery",
"infrastructural"
],
"tagged_values": {
"Service Discovery": "Eureka",
"Port": 8010
}
},
{
"name": "user_service",
"stereotypes": [
"internal"
],
"tagged_values": {
"Port": 8016
}
},
{
"name": "kafka",
"stereotypes": [
"message_broker",
"infrastructural"
],
"tagged_values": {
"Message Broker": "Kafka",
"Port": 9092
}
},
{
"name": "mailer",
"stereotypes": [
"internal",
"local_logging"
],
"tagged_values": {
"Port": 8020
}
},
{
"name": "reminder",
"stereotypes": [
"internal",
"local_logging"
],
"tagged_values": {
"Port": 8015
}
},
{
"name": "api_gateway",
"stereotypes": [
"gateway",
"circuit_breaker",
"resource_server",
"infrastructural",
"csrf_disabled"
],
"tagged_values": {
"Circuit Breaker": "Hystrix",
"Port": 8018
}
},
{
"name": "oauth",
"stereotypes": [
"authorization_server",
"tokenstore",
"infrastructural",
"circuit_breaker"
],
"tagged_values": {
"Authorization Server": "Spring OAuth2",
"Port": 8017,
"Circuit Breaker": "Hystrix"
}
},
{
"name": "proxy",
"stereotypes": [
"web_application",
"infrastructural"
],
"tagged_values": {
"Web Application": "Nginx",
"Port": 80
}
},
{
"name": "zookeeper",
"stereotypes": [
"configuration_server",
"infrastructural"
],
"tagged_values": {
"Configuration Server": "ZooKeeper",
"Port": 2181
}
},
{
"name": "jmx_monitoring",
"stereotypes": [
"internal"
],
"tagged_values": {}
},
{
"name": "todo_infra",
"stereotypes": [
"internal"
],
"tagged_values": {}
}
],
"information_flows": [
{
"sender": "admin",
"receiver": "config_server",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "config_server",
"receiver": "eureka_server",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "eureka_server",
"receiver": "admin",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "admin",
"receiver": "user_service",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "config_server",
"receiver": "user_service",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "admin",
"receiver": "mailer",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "config_server",
"receiver": "mailer",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "mailer",
"receiver": "eureka_server",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "kafka",
"receiver": "mailer",
"stereotypes": [
"restful_http",
"message_consumer_kafka"
],
"tagged_values": {
"'Consumer Topic'": "\"todo-mail\""
}
},
{
"sender": "reminder",
"receiver": "eureka_server",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "admin",
"receiver": "reminder",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "config_server",
"receiver": "reminder",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "reminder",
"receiver": "kafka",
"stereotypes": [
"restful_http",
"message_producer_kafka"
],
"tagged_values": {
"'Producer Topic'": "\"todo-mail\""
}
},
{
"sender": "eureka_server",
"receiver": "api_gateway",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "admin",
"receiver": "api_gateway",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "config_server",
"receiver": "api_gateway",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "api_gateway",
"receiver": "user_service",
"stereotypes": [
"restful_http",
"load_balanced_link",
"feign_connection"
],
"tagged_values": {
"'Load Balancer'": "\"Ribbon\""
}
},
{
"sender": "config_server",
"receiver": "oauth",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "oauth",
"receiver": "user_service",
"stereotypes": [
"restful_http",
"auth_provider",
"load_balanced_link",
"feign_connection"
],
"tagged_values": {
"'Load Balancer'": "\"Ribbon\""
}
},
{
"sender": "oauth",
"receiver": "eureka_server",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "admin",
"receiver": "oauth",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "user",
"receiver": "proxy",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "proxy",
"receiver": "user",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "proxy",
"receiver": "api_gateway",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "zookeeper",
"receiver": "kafka",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "proxy",
"receiver": "logstash",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "user_service",
"receiver": "logstash",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "reminder",
"receiver": "logstash",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "eureka_server",
"receiver": "logstash",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "api_gateway",
"receiver": "logstash",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "oauth",
"receiver": "logstash",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "admin",
"receiver": "logstash",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "config_server",
"receiver": "logstash",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
},
{
"sender": "mailer",
"receiver": "logstash",
"stereotypes": [
"restful_http"
],
"tagged_values": {}
}
],
"external_entities": [
{
"name": "user",
"stereotypes": [
"user_stereotype",
"entrypoint",
"exitpoint"
],
"tagged_values": {}
},
{
"name": "logstash",
"stereotypes": [
"logging_server",
"exitpoint"
],
"tagged_values": {
"Logging Server": "Logstash",
"Port": 5044
}
}
]
}
Model Items
The Application consists of 149 elements:
| Element | Count |
|---|---|
| Services | 13 |
| External Entities | 2 |
| Information Flows | 34 |
| Annotations | 100 |
| Total Items | 149 |
Model Representations
Open the model in the following formats:
Traceability
Open the traceability information for all model items:
Security Rules
The following table shows the application’s adherence to the 17 architectural security rules. The last column provides model variants that adhere to the rule for each rule that is initially violated.
| Rule ID | Verdict | Evidence | Model Variant |
|---|---|---|---|
| R1 | Evidence | ||
| R2 | Evidence | Variant | |
| R3 | Evidence | ||
| R4 | Evidence | Variant | |
| R5 | Evidence | ||
| R6 | Evidence | Variant | |
| R7 | Evidence | Variant | |
| R8 | Evidence | Variant | |
| R9 | Evidence | Variant | |
| R10 | Evidence | Variant | |
| R11 | Evidence | Variant | |
| R12 | Evidence | Variant | |
| R13 | Evidence | ||
| R14 | Evidence | ||
| R16 | Evidence | ||
| R17 | Evidence | Variant | |
| R18 | Evidence | Variant |
Evidence and explanations for rule decisions
R1
Rule is partially adhered to:
- API-Gateway provided by @EnableFeignClients and the annotated @FeignClients,
- No single-entry point as separate access to auth-server as defined in README.md authentication/retrieving token process uses two different ports (8017 is auth server, 8018 is api gateway),
- authorizes with @EnableResourceServer annotation
Artifacts:
- BasicApplication.java: Line: 8
- TodoClient.java: Line: 16
- UserClient.java: Line: 16
- oauth.properties: Line: 1
- api-gateway.properties: Line: 1
- OAuth2ResourceServerConfiguration.java: Line: 19
R2
Rule is violated:
- Gateway does authorize per @EnableResourceServer annotation,
- Downstream services do not include annotation anywhere
Artifacts:
- OAuth2ResourceServerConfiguration.java: Line: 19
R3
Rule is adhered to:
- The @EnableAuthorizationServer annotation is present,
- JWT as tokens as JwtAuthenticationConverter at the authorization server function present,
- JWTs are validated by Gateway as JwtAuthenticationConverter includes insertion of public key and @EnableResourceServer annotation. Thus decoupled from the auth server.
Artifacts:
- OAuth2ServerConfiguration.java: Line: 24
- JwtServerConfiguration.java: Line: 27
- OAuth2ResourceServerConfiguration.java: Line: 19
- JwtConfiguration.java: Line: 35
R4
Rule is violated: Identity representations are not used for all levels of authorization and authentication as only API Gateway authorizes and does not get transformed. See Rule 2 arguments.
R5
Rule is adhered to: Tokens are validated at the API Gateway per annotation and public key inserted at JwtAuthenticationConverter.
R6
Rule is violated: There is no functionality present that enforcecs any consequences for a specific amount of failed login attempts
R7
Rule is violated: There are no certificates in the repository and no “server.ssl.key-store”/”server.ssl.trust-store” arguments inserted in the yml of the API gateway
Artifacts:
- api-gateway.properties: Line: 1
R8
Rule is violated: See Rule 7 comment, but the arguments are not existent in any other yml configuration
R9
Rule is adhered to: This microservice application deploys the ELK stack (Elasticsearch, Logstash, Kibana) as a logging mechanism. Logstash is deployed as a central logging subsystem. Logstash then sends the formatted data to an Elasticsearch indexing server. Additionally Kibana is deployed as a monitoring dashboard on top of the indexing server.
Artifacts:
- infra-docker-compose.yml: Line: 4
R10
Rule is adhered to:
- Beats configuration in each service that specifies the ElasticSearch container,
- Dockerfile that installs beats with said configuration,
- then starts own service in Dockerfile
Artifacts:
R11
Rule is violated: No sanitization mechanism to be found, but also not needed as there is no sensitive data logged.
Artifacts:
R12
Rule is violated: Kafka is used as message broker, however between services and not used for the logging subsystem.
Artifacts:
- WebSocketConfig.java: Line: 11
R13
Rule is adhered to: Hystrix is enabled using the @EnableHystrix annotation for any routes retrieved by integrated Load balancer from Feign which is Ribbon.
Artifacts:
- BasicApplication.java: Line: 10
R14
Rule is adhered to: The gateway automatically performs load balancing using Ribbon integrated into Feign clients.
Artifacts:
- BasicApplication.java: Line: 9
R15
This rule is not applicable: Not a service mesh deployment.
R16
Rule is adhered to:
- Registry Service (Eureka) present with @EnableEurekaServer
- Starting the Eureka Server via Docker-Compose -> Deployment on dedicated server possible
Artifacts:
R17
Rule violated: There is no HTTP basic password password listed in any YML-Configuration of format username:password@here-location-of-eureka-server at “eureka.client.serviceUrl.defaultZone”.
Artifacts:
- api-gateway.properties: Line: 3
R18
Rule is violated: No secret manager is deployed.